Informatics Core
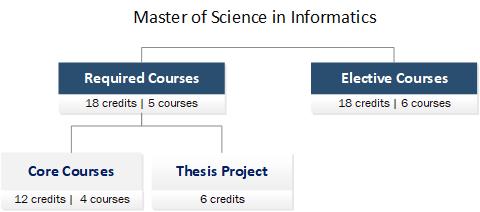
The Informatics core consists of four courses and a Master’s thesis:
Covers the concepts, principles, issues and techniques for managing corporate data resources. Students learn techniques for managing the design and development of large database systems including logical data models, concurrent processing, database administration, data distribution, integrity, security and access are examined. Topics include data modeling, SQL and database architectures and implementations, data warehousing, data cleansing, and data mining. Major database products like Oracle, DB2, SQL Server 2005, along with open source solutions, are comparatively presented and evaluated. Prerequisites: None Credits: 3
Covers telecommunications fundamentals, including data, voice, image, and video. The concepts, models, architectures, protocols, standards, and security for the design, implementation, and management of digital networks are examined. The essentials of local area networks (LAN), metropolitan area networks (MAN), and wide area networks (WAN) are covered, as well as both transmission and switching efficiency. Also covered are regulatory and technical environments. Topics include security and authentication, network operating systems, e-commerce and associated web sites and practices, and middleware for wireless systems, multimedia, and conferencing. Prerequisites: None Credits: 3
Covers the systems development life cycle, analysis and design techniques, requirements collection and structuring, process modeling, data modeling, design of interface and data management, and middleware design. Students will use current methods, tools, and methodologies including the latest UML platforms, prototyping & visual development. Prerequisites: None Credits: 3
Presents management and strategic perspectives for aligning competitive strategy, core competencies, and information systems. The course explores the development and implementation of policies and plans to achieve organizational goals. It defines the systems that support the operational, administrative, and strategic needs of the organization, its business units, and individual employees. Students learn approaches to managing the information systems function in organizations, including examination of the dual challenges of effectively controlling the use of well-established information technologies, while experimenting with selected emerging technologies. Prerequisites: None Credits: 3
Aims to expose students to real-life situations encountered in business environments through the development of original and practical applications. The Thesis will enable students to gain experience in all phases of the implementation and management of information systems, applying the knowledge and skills they have acquired in different course modules. Alternatively, students can opt to do an in-depth study of a research topic, including bibliographic review and the development and implementation of the technological aspects of the topic, as preparation for writing the thesis. Students select a topic of interest and a personal supervisor for completing the Master Thesis. Prerequisites: Completion of all core requirements or permission by program director. Credits: 6
This requirement consists of 18 graduate credits. Τhese five courses are the basis for an Informatics degree since they form the basis of modern information systems. The Master’s Thesis aims to expose students to real-life situations encountered in business environments through the development of original and practical applications. Alternatively, students who are inclined towards research can learn advanced techniques and practices used in Informatics by participating in faculty-supported research.
Business Computing and Big Data Analytics
Students may concentrate in the field of Business Computing and Big Data Analytics by selecting 6 elective courses from the following group of courses:
This course provides instruction in all aspects of e-business operations, from front-office marketing, commerce, sales and customer service, to back-office operations, including human resource administration and supply-chain management. Additionally, emphasis will be placed on the use of e-business models to enable the Internet to function as a trusted medium for carrying on day-to-day business activities and enhance the performance of an organization. Prerequisites: None Credits: 3
Offers students the opportunity to explore modern design methodologies that allow for the development of scalable and decoupled components. Technologies such as XML, Web Services and Enterprise Development Environments will be investigated. The course investigates current IT trends and methodologies that yield efficient and effective solutions to sustain a competitive edge in today’s businesses. Students will be able to synthesize and select the appropriate technology to engineer modern enterprise solutions. Prerequisites: None Credits: 3
Explores programming techniques for web and e-commerce program development. The courses develops students’ programming skills with HTML, dynamic HTML, animation, graphics, JavaScript, VBScript, CSS, XSL, ASP, ActiveX Data Objects, session tracking, cookies and shopping carts. Students are shown applications of e-commerce programming to various e-business models. Prerequisites: None Credits: 3
Covers the fundamentals of data warehousing architecture and the issues planning, designing, building, populating, and maintaining a successful data warehouse. In addition, data mining is introduced and linked with the data warehouses. Various topics include logical design of a data warehouse, the data staging area, and the use of multidimensional analysis using OLAP techniques, as well as future trends in data mining. Various data mining systems are presented. (3 Credits)
Introduces the basic concepts and methods of artificial intelligence (AI) and neural networks (NNs) from a computer science perspective. Students learn how to design AI and NNs models for different applications. Emphasis is given on the selection of data representations and algorithms useful in the design and implementation of intelligent systems. Students participate in lectures and discussions on various topics, including heuristic, logical and probabilistic reasoning, planning, learning, and perception. Advanced topics are selected from areas such as robotics, vision and neural networks. (3 Credits)
This course covers the basics of graph theory; the objective is to build the strong background required for students enrolled in the social networks program. The material to be covered includes: Fundamental concepts of graphs; Classification of nodes and links; Vector spaces and graphs; Topological parameters: packings and coverings; Connectivity; Hamilton graphs; Graph factorization; Graph coloring; partite graphs; and folding. Prerequisites: None Credits: 3
This advanced course in business analytics introduces graduate students to corporate data preparation, data discovery and report creation employing SAS Viya platform. This course can also help preparing the graduate student to take the following SAS certification exams: SAS certified specialist: SAS visual business analytics 7.5/8.3. Prerequisites: None, Credits: 3
This course presents models, methods, and techniques for studying and analyzing Criminal Networks. More specifically, mathematical and computer science methods and techniques to fight crime are presented, such as information harvesting and integration, Modeling Criminal Activity, Strength of Structures of Small Sizes, Qualitative and Quantitative Temporal Reasoning, and others. (3 Credits)
The objective of this course is to present the fundamentals of pattern analysis and detection in numerical data. Topics include techniques for handling multidimensional data of various types and scales along with algorithms for clustering and classifying data. Decision theory, statistical classification, maximum likelihood and Bayesian estimation, Linear Discriminant Functions, Multilayer Neural Networks and Stochastic Methods will be also discussed. Prerequisites: None Credits: 3
This course introduces students to the basic concepts and techniques in social networks analysis. Students learn how and when to apply different metrics for social network analysis. Topics to be covered include: identifying key individuals and groups in social systems; detecting and generating fundamental network structures, studying hidden communities, and modeling growth and diffusion processes in networks. Students will learn how to use different tools for social network analysis. Prerequisites: None Credits: 3
Game theory is a branch of Mathematical Economics that studies strategic interactions amongst rational decision makers. Traditionally, game theoretic tools have been applied to solve problems in Economics, Business, Political Science, Biology, Sociology, Computer Science, Logic, and Ethics. In recent years, applications of game theory have been successfully extended to several areas of engineered / networked system such as wireline and wireless communications, static and dynamic spectrum auction, social and economic networks. This course is intended to provide students with a comprehensive treatment of game theory with specific emphasis on applications in Economics and Engineering. Prerequisites: None. Credits: 3
Covers the management of projects within an organizational context, including the processes related to initiating, planning, executing, controlling, reporting, and closing a project. Project integration, scope, time, cost, quality control, and risk management are also explored. Focus is given to the IT area. Hands-on experience on using a Project Management tool is provided. Prerequisites: None Credits: 3
This group of courses will provide students with the basic knowledge in the area of big data analysis and business computing, and will enable them to participate in research projects in the field. This group of courses also focuses on technical, organizational, and managerial issues at the enterprise level as a whole, on a day-to-day basis.
Applications and Software Development
Students may concentrate in the field of Applications and Software Development by selecting 6 elective courses from the following group of courses:
Addresses the role of management support systems in decision-making within organizations by combining data, sophisticated analytical models and tools, and user-friendly software into a single powerful system. Data from internal and external sources are examined to help monitor organizational performance, track activities of competitors, spot problems, identify opportunities, and forecast trends. Topics include data mining, artificial intelligence techniques, and agent technologies. Prerequisites: None Credits: 3
Introduces business processes and the integration of Enterprise Systems with a focus on the core modules of financial accounting, cost management, materials management, sales and distribution, and production planning and control. The course will build an understanding of enterprise system processes and configuration activities, which occur in companies using Enterprise Systems. Students will understand the business activities that these systems support, allowing them to be prepared for business, technical, or system support roles. Hands-on experience and demonstrations of successful Enterprise System such as SAP S/4HANA, will be provided so that students can put into practice the theory that supports business activities. Prerequisites: None Credits: 3
Covers object-oriented and procedural software engineering methodologies that bring together key technologies and insights for the development of robust, reliable, enterprise-class Web and distributed applications. Major technology solutions such as .NET and J2EE. are presented. Prerequisites: None Credits: 3
Students will gain an in-depth exposure to information technology hardware and software components and their interaction. A systems view of computer systems will be used to identify computer and telecommunication system components. Peripheral devices will be described and principles of operation will be studied and learned. The operating system software, including I/O drivers, and telecommunication applications and extensions to the operating system will be examined and utilized. Organization of the operating system will be studied to understand how concurrent processes, scheduling, memory management, and I/O are accomplished. Telecommunication devices will be identified and system integration considerations will be presented. Finally, switches, multiplexers, and media will be explored as basic components of telephone, LAN, and WAN systems. Prerequisites: None Credits: 3
Provides a detailed understanding of the principles and practices involved in the creation and implementation of user interfaces and, more specifically, the theory and practice of human computer interaction. Students learn how to design, implement, and evaluate human computer interaction and become familiar with the most common toolkits used in user interface design. The course focuses on usability and accessibility, presenting the most common usability methods and accessibility guidelines. Finally, a special section of the course is devoted to user interface design for ubiquitous devices such as mobiles, PDAs and Tablet PCs, while other emerging technologies will be examined. Prerequisites: None Credits: 3
Focuses on the principles, key ideas, and issues in the design and implementation of computer operating systems and distributes systems. The course covers topics such as concurrency and distributed communication, fault-tolerance, availability and persistence, and operating system structure. In addition, students focus on the principles used in the design of operating systems and distributed systems, and algorithms and data structures used in their implementation. Prerequisites: None Credits: 3
Introduces the theory and practice of programming language design. Topics presented include advanced language constructs, parallel programming, formal specification and implementation of programming languages, and compiler construction tools. In the context of the course, students design and implement a small and simple programming language. Prerequisites: None Credits: 3
Provides students with both a theoretical and a practical foundation in advanced software engineering concepts. In the theoretical part, students learn about the principles and methods of software engineering, including current and emerging software engineering practices and support tools. In the practical part, students become familiar with the development of software products from an industry perspective, including generation of appropriate documents under tight schedules and with limited resources. Prerequisites: None Credits: 3
This advanced course in business analytics introduces graduate students to corporate data preparation, data discovery and report creation employing SAS Viya platform. This course can also help preparing the graduate student to take the following SAS certification exams: SAS certified specialist: SAS visual business analytics 7.5/8.3. Prerequisites: None, Credits: 3
This group of courses will provide students with the required knowledge in the area of software and applications development, and will enable them to participate in research projects in the field. This group of courses covers the fields of User Interfaces development, Software development as well as development of operating systems.
Computer Networks and Security
Students may concentrate in the field of Information Security Management by selecting 6 elective courses from the following group of courses:
This course aims to familiarize students with the advancements in wireless and mobile networks using various methods such as lecture notes from the adopted textbook, various scientific papers and case studies for the new developments in the subject, hands-on-experience methods in class, and lectures by invited speakers who will share their experience. Key wireless topics such as radio frequency communications, infrared and Bluetooth networks, as well as wireless LANs, will be introduce and explained. Prerequisites: None Credits: 3
Covers the ten domains in the Information Security Common Body of Knowledge: Security Management Practices, Security Architecture and Models, Business Continuity Planning (BCP) and Disaster Recovery Planning (DRP), Law, Investigations, and Ethics, Physical Security, Operations Security, Access Control Systems and Methodology, Cryptography, Telecommunications, Network, and Internet Security. Prerequisites: None Credits: 3
Governance, Risk and Compliance (GRC) are key concerns for an organization. Related activities are integrated and aligned to provide a unified approach to such issues, reflecting management’s overall strategy and approach. Executive commitment and the overall management approach are critical for the success of an information security program. In this course, we examine methods for establishing and maintaining an information security governance framework. Risk assessment and risk management are key processes of this framework. Different approaches to information risk analysis are presented and compared. Finally, legal and regulatory compliance mandates the existence of specific controls to ensure an adequate level of security. Prerequisites: None Credits: 3
Cryptography plays a major role in securing information, communications and computer systems. Modern cryptographic algorithms are based on a solid mathematical basis. This course focuses more on the applications of cryptography in securing information systems rather than the mathematical background. We examine several classes of cryptographic algorithms and how they can be used to provide different security services, such as confidentiality and integrity. Issues related to creating, distributing and managing cryptographic keys are also discussed. Prerequisites: None Credits: 3
The security threats and risks that govern computer systems and networks can be mitigated by using a variety of security models, mechanisms and protocols. Such mechanisms are used to implement security policies that are defined in a risk management strategy. Designing security architecture is a critical task that includes securing hardware, software and networks. This course introduces security models and the concept of subjects and objects in order to discuss authorization and access control. Case studies of how authentication and access control are implemented in real-life systems are also presented. Security risks that are related to networks are equally important. We define secure communication channels and present known and established network security protocols (SSH, SSL, IPSec, etc.). Special cases such as wireless and mobile networks are also examined to demonstrate how traditional security architectures can be adapted to facilitate different requirements. Prerequisites: None Credits: 3
Business Continuity Planning is an integral part of an information security management program. Since we cannot achieve 100% security, it is essential to have established all necessary procedures in order to identify and respond to an incident, which will sooner or later occur, ensuring the continuity of business. Incident management is only one aspect of Business Continuity. Designing, developing and implementing a business continuity plan is thoroughly explained in this course, identifying all necessary steps from executing a business impact assessment to defining roles, responsibilities and continuity procedures. In this course we also discuss Disaster Recovery Planning, covering all necessary processes required to recover business-critical infrastructure in the event of a disaster. Prerequisites: None Credits: 3
Software applications are often characterized as the cement of our times due to the high prevalence of computer systems in all aspects of our lives: banking, health, transportation, retail, even “smart home” systems. As a result, managing application security risks is a quite critical aspect of information security. This course aims to justify the importance of application security, firstly by analyzing how security can be integrated in the software development lifecycle. We demonstrate methods to identify vulnerabilities and discuss techniques that can be used to mitigate them and improve the overall security of software applications. Closely coupled with applications are databases that support them and facilitate data storage, retrieval and corresponding transactions. Concurrency control is a critical issue in database security. We discuss methods for concurrency control and several aspects of database security, focusing on relational databases. Prerequisites: None Credits: 3
This advanced course in business analytics introduces graduate students to corporate data preparation, data discovery and report creation employing SAS Viya platform. This course can also help preparing the graduate student to take the following SAS certification exams: SAS certified specialist: SAS visual business analytics 7.5/8.3. Prerequisites: None, Credits: 3
Hellenic American University’s Master of Science in Informatics (MSI) is in alignment with the ISACA Model Curriculum for Information Security Management, 2nd Edition. Graduates of the program who have selected this group of courses qualify for one year of work experience towards the Certified Information Security Manager (CISM designation). The program is listed as one of the two unique programs worldwide that are aligned with the ISACA curriculum in Information Security Management.

